By default Cisco uses HDLC encapsulation on Serial interfaces. We are going to setup a simple PPP link with Authentication.
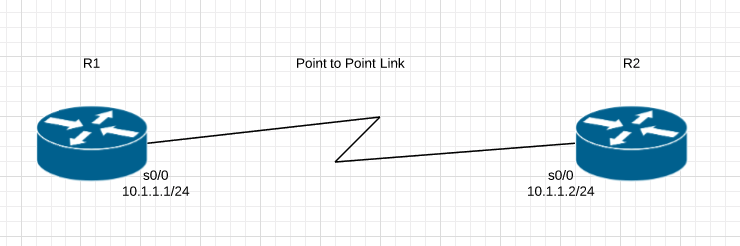
R1#show int serial 0/0 Serial0/0 is up, line protocol is up Hardware is GT96K Serial Internet address is 10.1.1.1/24 MTU 1500 bytes, BW 1544 Kbit/sec, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation HDLC, loopback not set Keepalive set (10 sec) Last input 00:00:09, output 00:00:07, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: weighted fair
R2#show int serial 0/0 Serial0/0 is up, line protocol is up Hardware is GT96K Serial Internet address is 10.1.1.2/24 MTU 1500 bytes, BW 1544 Kbit/sec, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation HDLC, loopback not set Keepalive set (10 sec) Last input 00:00:05, output 00:00:06, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: weighted fair
We have to change that to PPP encapsulation on both sides, other wise there will be a encapsulation mismatch and the Interface will remain up but the line protocol will be down.
R1(config-if)#encapsulation ? frame-relay Frame Relay networks hdlc Serial HDLC synchronous lapb LAPB (X.25 Level 2) ppp Point-to-Point protocol smds Switched Megabit Data Service (SMDS) x25 X.25
R1(config-if)#encapsulation ppp
R1(config-if)# *Mar 1 00:05:27.739: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to down R1(config-if)#exit R1(config)#exit R1#sh int serial 0/0 Serial0/0 is up, line protocol is down Hardware is GT96K Serial Internet address is 10.1.1.1/24 MTU 1500 bytes, BW 1544 Kbit/sec, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation PPP, LCP Listen, loopback not set
R2(config)#int serial 0/0 R2(config-if)#encapsulation ppp R2(config-if)#exit R2(config)#exit R2#sh int serial 0/0 Serial0/0 is up, line protocol is up Hardware is GT96K Serial Internet address is 10.1.1.2/24 MTU 1500 bytes, BW 1544 Kbit/sec, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation PPP, LCP Open
We should move from HDLC to PPP because PPP has some features that HDLC doesn’t for example, Authentication options, error detection and error recovery features.
Password Authentication Protocol (PAP) and Challenge Authentication Protocol (CHAP)
PAP is very passive authentication, where as CHAP actively asks who are you?
PAP also sends username and password in Clear Text.
Here is how to configure CHAP on both routers
The username is the Hostname of the Peer Router you are authenticating to. The passwords must match.
R1(config)#username R2 password TPW R1(config)#int serial 0/0 R1(config-if)#ppp authentication chap
R2(config)#username R1 password TPW R2(config)#int serial 0/0 R2(config-if)#ppp authentication chap
Most likely if there is a issue its with the passwords mismatching, but you can always use the command:
R1#debug ppp authentication