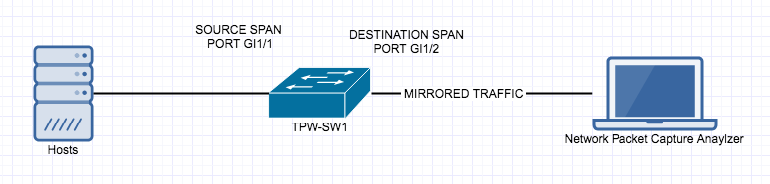
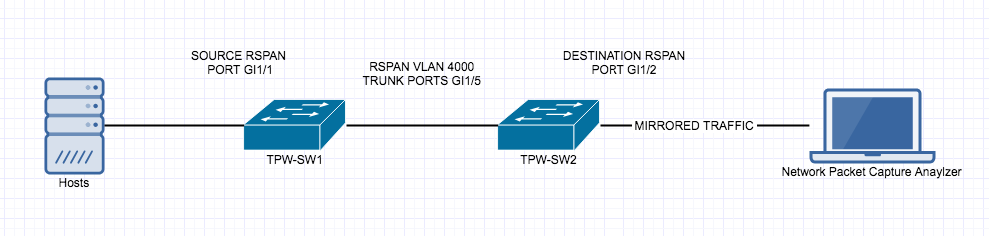
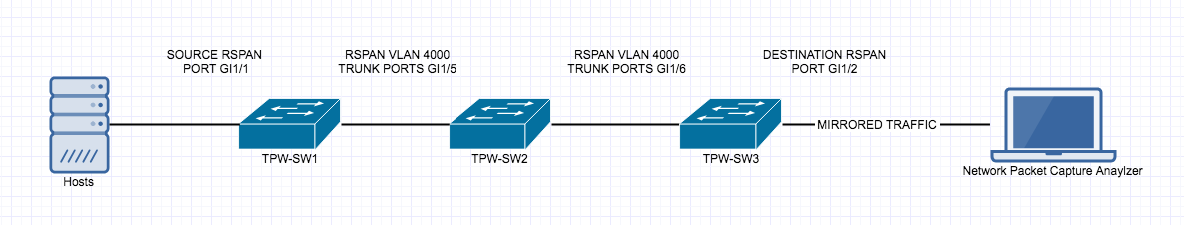
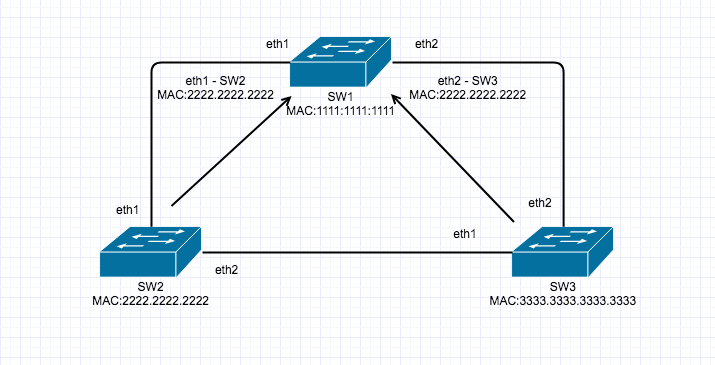
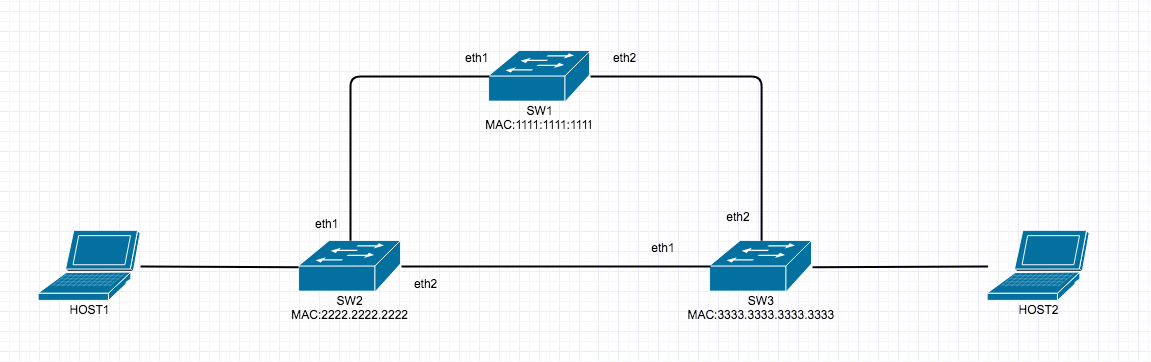
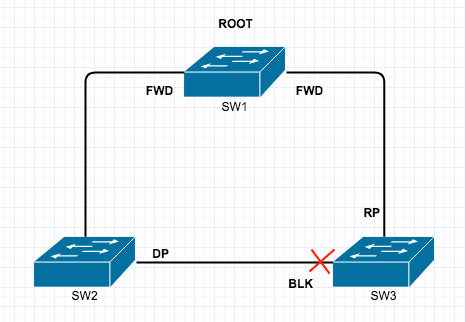
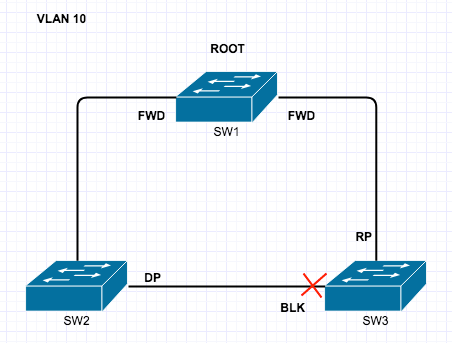
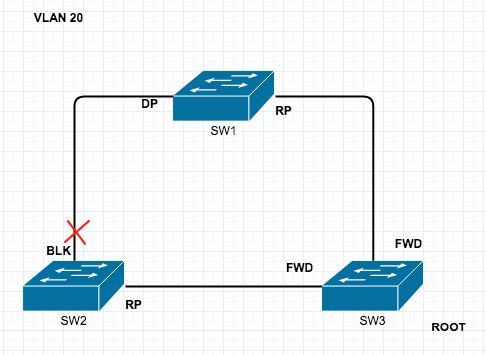
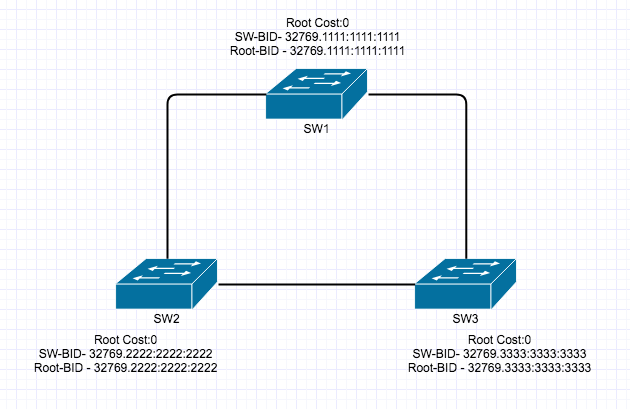
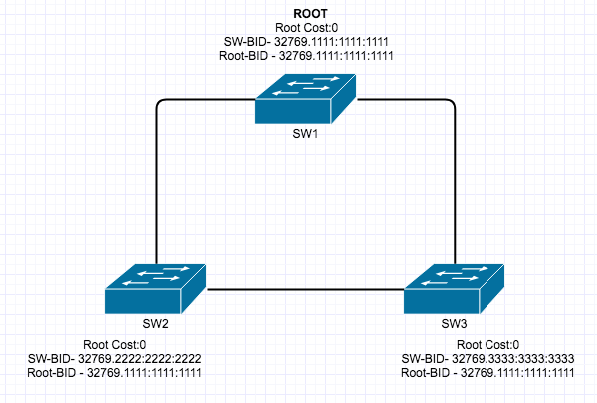
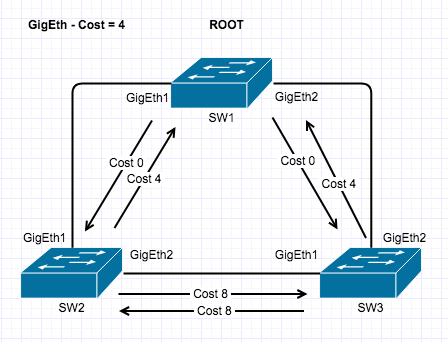
Private VLAN’s are a very interesting and mostly used for Network segmentation and fun concept but it can take a little to get your head around, so here goes.
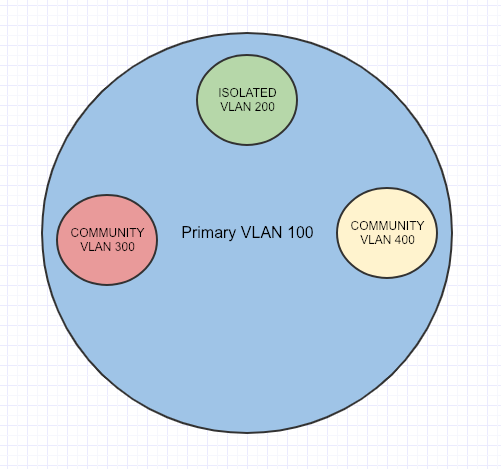
Private VLAN’s split a VLAN into Sub-VLANs, called Primary and Secondary. Secondary VLAN’s have 2 different types : Isolated and Community.
In this example the Primary VLAN is 100 and the Secondary VLAN’s are Isolated VLAN 200, Community VLAN 300 and Community VLAN 400.
An important port to know about before beginning is called the Promiscuous Port. It acts like a Gateway that routes Primary and Secondary-VLAN traffic, and all Secondary-VLAN traffic must pass through the Promiscuous Port.
Isolated ports can only talk to the Primary VLAN through a Promiscuous Port (Uplink/Gateway Port)
Community ports can talk to each other, if they are in the same Community Secondary-VLAN.
VTP must be set to transparent mode for Private VLAN’s to work.
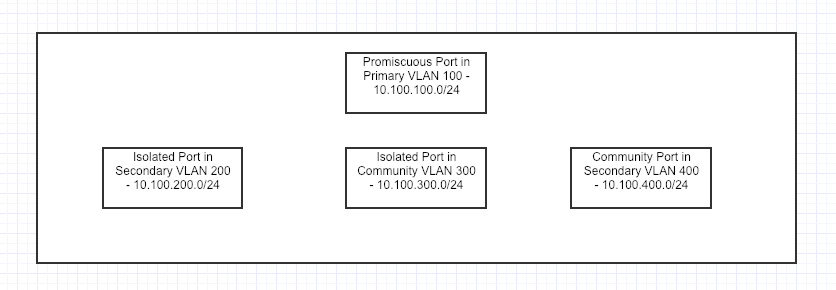
Here is how to configure Private VLAN’s
First we need to configure the Primary VLAN
TPW-SW1(config)#vlan 100 TPW-SW1(config-vlan)#private-vlan primary TPW-SW1(config-vlan)#exit
Configure the Isolated VLAN
TPW-SW1(config)#vlan 200 TPW-SW1(config-vlan)#private-vlan isolated TPW-SW1(config-vlan)#exit
Configure the Community VLAN’s
TPW-SW1(config)#vlan 300 TPW-SW1(config-vlan)#private-vlan community TPW-SW1(config-vlan)#exit TPW-SW1(config)#vlan 400 TPW-SW1(config-vlan)#private-vlan community TPW-SW1(config-vlan)#exit
Now we have to associate the Primary VLAN to the Isolated and Community VLAN’s
TPW-SW1(config)#vlan 100 TPW-SW1(config-vlan)#private-vlan association 200 TPW-SW1(config-vlan)#private-vlan association 300 TPW-SW1(config-vlan)#private-vlan association 400
This is where we configure for fa0/1 as the Promiscuous Port
TPW-SW1(config-if)# int fa0/1 TPW-SW1(config-if)#switchport mode private-vlan promiscuous
We have to tell the Promiscuous Port that it is associated with the (Isolated and Community VLAN’s) that it can also see and talk to them appropriately.
TPW-SW1(config-if)#switchport private-vlan host-association 100 200,300,400 TPW-SW1(config-if)#exit
Configure fa0/2 and fa0/7 as the Isolated port, but also about its Primary VLAN 100
TPW-SW1(config-if)# int fa0/2 TPW-SW1(config-if)#switchport mode private-vlan host TPW-SW1(config-if)#switchport private-vlan host-association 100 200 TPW-SW1(config-if)#exit TPW-SW1(config-if)# int fa0/7 TPW-SW1(config-if)#switchport mode private-vlan host TPW-SW1(config-if)#switchport private-vlan host-association 100 200 TPW-SW1(config-if)#exit
Configure fa0/3 and 4 as community ports, but also about its Primary VLAN 100
TPW-SW1(config)#int range fa0/3 - 4 TPW-SW1(config-if-range)# TPW-SW1(config-if-range)# switchport mode private-vlan host TPW-SW1(config-if-range)# switchport private-vlan host-association 100 300 TPW-SW1(config-if-range)# exit
Configure fa0/5 and 6 as community ports, but also about its Primary VLAN 100
TPW-SW1(config)#int range fa0/5 - 6 TPW-SW1(config-if-range)# TPW-SW1(config-if-range)# switchport mode private-vlan host TPW-SW1(config-if-range)# switchport private-vlan host-association 100 400 TPW-SW1(config-if-range)# exit
You can confirm the Private VLAN’s are setup correctly with the following show command
TPW-SW1#show vlan private-vlan Primary Secondary Type Ports ------- --------- ----------------- ---------------------------------- 100 200 isolated fa0/2, fa0/7 100 300 community fa0/3, fa0/4 100 400 community fa0/5, fa0/6
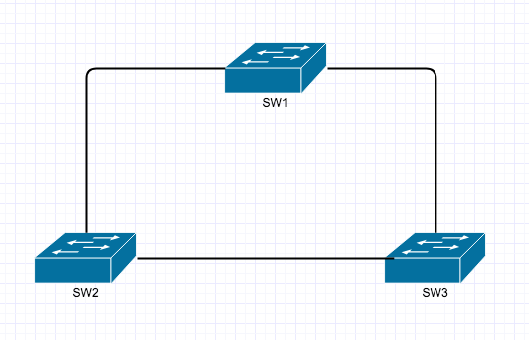
Here is the topology of what was just built.
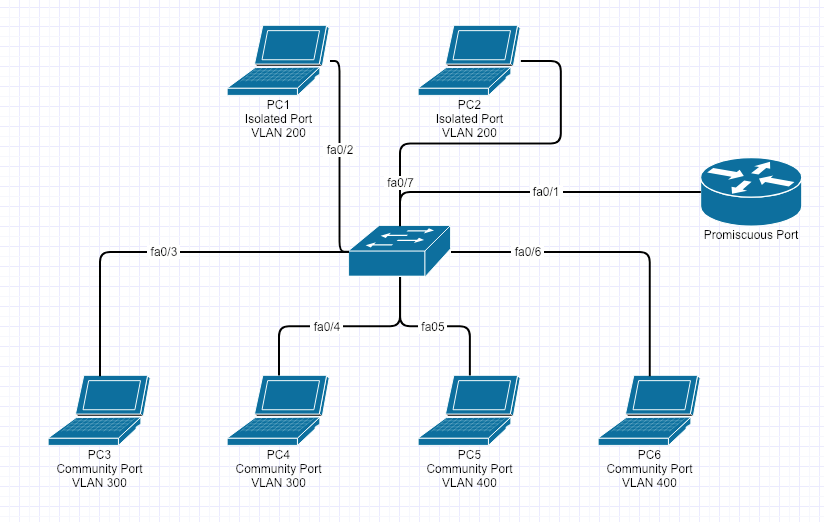
Here is a table of what can talk to each other
PC
| Computer | PC1 – Isolated – VLAN 200 | PC2 – Isolated – VLAN 200 | PC3 – Community VLAN 300 | PC4 – Community VLAN 300 | PC5 – Community VLAN 400 | PC6 – Community VLAN 400 |
| PC1 – Isolated – VLAN 200 | YES | NO | NO | NO | NO | NO |
| PC2 – Isolated – VLAN 200 | NO | YES | NO | NO | NO | NO |
| PC3 – Community VLAN 300 | NO | NO | YES | YES | NO | NO |
| PC4 – Community VLAN 300 | NO | NO | YES | YES | NO | NO |
| PC5 – Community VLAN 400 | NO | NO | NO | NO | YES | YES |
| PC6 – Community VLAN 300 | NO | NO | NO | NO | YES | YES |